Following Twitter’s somewhat shambolic rebrand to X last year[1], a technical blunder by the organisation on 8 April created a bit of a headache for some brand owners. An addition to the platform was intended to replace any links containing references to ‘twitter.com’ with copies instead reading ‘x.com’, but the implementation was rolled out as a clumsy blanket ‘copy-and-replace’. This meant that the modification affected any domain name ending with ‘twitter.com’. The error presented the potential for a platform-specific style of phishing attack, where any brand website ending with ‘x.com’ could in theory be impersonated using an equivalently named domain ending with ‘twitter.com’. One early report involved the registration of fedetwitter[.]com, to which links would have appeared in tweets as links to fedex[.]com, the legitimate domain name of the logistics organisation[2].
The issue was fixed relatively quickly, but not before a resulting spike of ‘-twitter’ registrations had taken place. These were by both brand owners as defensive actions, and by third parties, potentially with a view to launching an attack or, in some cases, as a way of drawing attention to the error. In this article, we look at the batch of domain registrations relevant to this incident, providing also a case study of the power of domain-monitoring tools which are able to be configured to inspect specific domain-name patterns.
In total, over 2,500 domains with second-level names (SLDs, i.e. the part to the left of the dot) ending with ‘twitter’ are currently registered, according to versions of the domain zone files downloaded on 11-Apr-2024. Of these, 71 show domain creation dates in the three-day period between 08 and 10-Apr-2024, a marked increase on the pre-existing ‘background’ levels of activity (Figure 1).
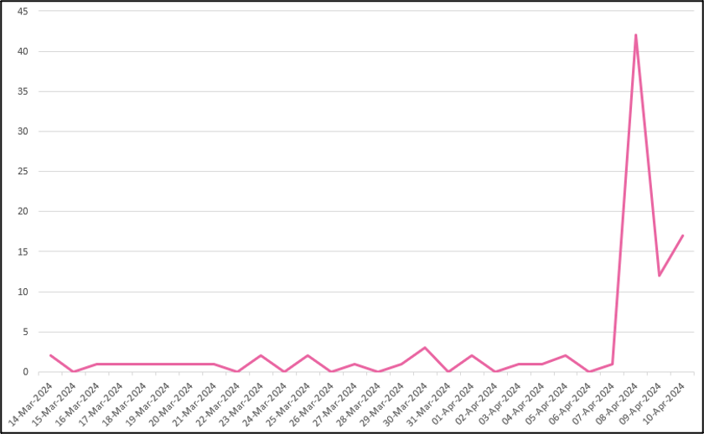
Figure 1: Daily numbers of registrations of domains with SLDs ending with ‘twitter’
Of these, a significant proportion appear to have been registered to take advantage of the Twitter/X string-replacement issue to target the websites of well-known brands, with examples including ametwitter[.]com, carfatwitter[.]com, cinepletwitter[.]com, citritwitter[.]com, clorotwitter[.]com, dropbotwitter[.]com, duretwitter[.]com, equifatwitter[.]com, fedetwitter[.]com, firefotwitter[.]com, firefotwitter[.]site, fotwitter[.]com, goodrtwitter[.]com, hbomatwitter[.]com, horotwitter[.]com, imatwitter[.]com, indetwitter[.]com, kleenetwitter[.]com, linutwitter[.]com, netflitwitter[.]com, nutanitwitter[.]com, roblotwitter[.]com, roletwitter[.]com, space-twitter[.]com, spotetwitter[.]com, square-enitwitter[.]com, timetwitter[.]com, turbotatwitter[.]com, witwitter[.]com, xbotwitter[.]com, xerotwitter[.]com and yandetwitter[.]com (targeting – respectively – amex[.]com, carfax[.]com, etc.). Examples were also found pertaining to other content (including adult material, with the dataset including gaysetwitter[.]com and setwitter[.]com).
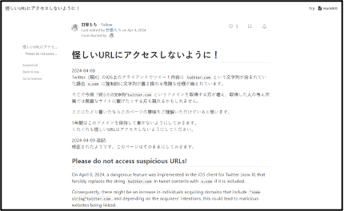
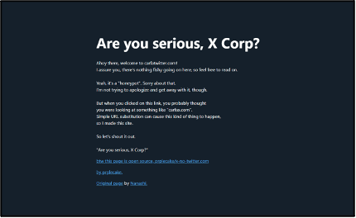
Of the 71 sites registered since 08-Apr-2024, only one (ametwitter[.]com) was found to resolve to content relating to the brand in question (American Express, ‘amex’), and may thereby pose a potential threat (Figure 2). A number of others were found to resolve to warning pages highlighting the risk of misdirection (Figure 3).

Figure 2: Live content on ametwitter[.]com as of 11-Apr-2024
|
|
|
|
|
|
 |
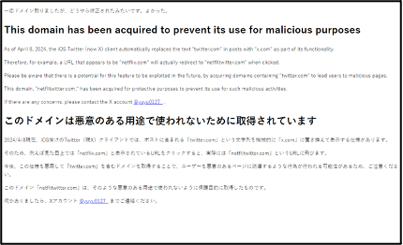 |
Figure 3: Live ‘warning’ pages as of 11-Apr-2024 (SLDs: apetwitter, bitmetwitter, carfatwitter, citritwitter, equifatwitter, netflitwitter)
The remainder of the sites appear to pose no serious risk currently, but may have been ‘weaponised’ for subsequent use in a brand-impersonation attack if the vulnerability had not been rectified by X (together with other registrations which might have arisen). The findings highlight the importance of ongoing proactive brand monitoring which is sufficiently configurable to be able to cover relevant brand variants in response to the emergence of specific issues.
[1] https://www.iamstobbs.com/opinion/x-trademarks-the-spot-not-a-textbook-example-of-a-successful-rebranding-exercise
[2] https://krebsonsecurity.com/2024/04/twitters-clumsy-pivot-to-x-com-is-a-gift-to-phishers/
Send us your thoughts:
Would you like to read more articles like this?
Building 1000
Cambridge Research Park
CB25 9PD
Fax. 01223 425258
info@iamstobbs.com
Privacy policy
German office legal notice
Cookie Declaration
Complaints Policy
Copyright © 2022 Stobbs IP
Registered Office: Building 1000, Cambridge Research Park, Cambridge, CB25 9PD.
VAT Number 155 4670 01.
Stobbs (IP) Limited and its directors and employees who are registered UK trade mark attorneys are regulated by IPReg www.ipreg.org.uk