In the previous articles in this series[1],[2], we have considered the emergence of new links between content in the classic Web2 (‘standard’ website and Internet) environment and the decentralised, blockchain-based world of Web3 (including blockchain domains, cryptocurrency and NFTs). In this follow-up, we consider how additional insights on links between content across these environments can be gained through investigation and clustering techniques.
One of the principal appeals of Web3 content is the opportunity for high levels of anonymity (part of the picture involved in a desire for lower restriction and regulation), and a lack of ties to ‘real-world’ contact details. However, this does not mean that no open-source intelligence (OSINT)-style techniques can be applied. Many of the characteristics associated with Web3 content – such as cryptocurrency wallet addresses – are unique and distinctive, and can be tied to other findings where the same details are used, and can imply (for example) that a particular entity may be associated with multiple infringements.
In this article, we present two anonymised ‘mini’ case studies illustrating how these types of techniques can be applied. Key to this process is the existence of publicly available databases (‘ledgers’) of information relating to Web3 content, which can be accessed through Web2 infrastructure. One such example is the etherscan.io website.
The case studies concern instances where bad actors were infringing particular marks (referred to in this article as Brand1 and Brand2), to promote cryptocurrencies. This is similar to the examples presented in Part 2 of this series. The first case made use of an associated infringing blockchain domain (Brand1deployer.eth) for which details were available on the etherscan.io public ledger.
The results of a search for the blockchain domain name bring up a number of unique strings (‘hashes’) relating to the domain and its registrant (Figure 1).
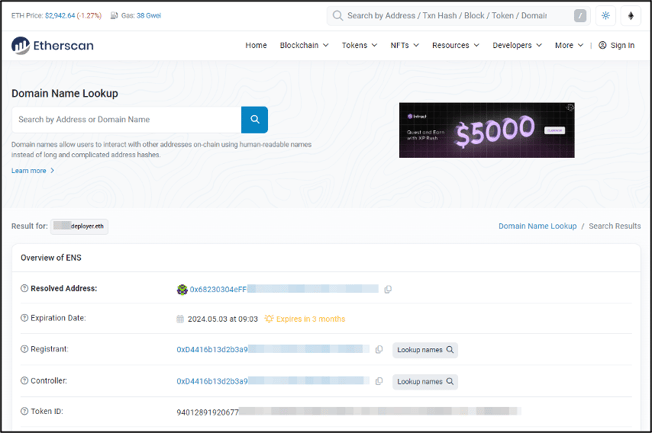
Figure 1: Results of a search for Brand1deployer.eth on etherscan.io
Clicking on the ‘resolved address’ string for the domain brings up an additional page, giving details of transactions made to and from the domain / user (Figure 2).
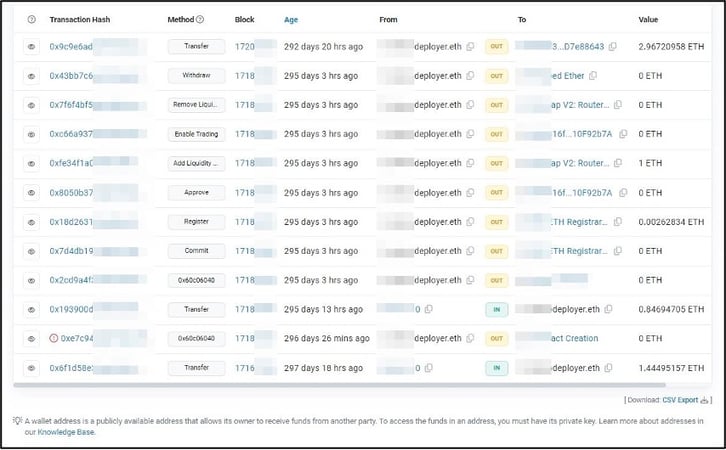
Figure 2: Extracts from the etherscan.io page giving details of transactions associated with Brand1deployer.eth
In this case, the fourth row from the bottom is the most significant; the content of the ‘To’ column reads ‘Create: Brand1’, indicating that this transaction is associated with creation of the ‘Brand1’-infringing smart contract (a blockchain program set to run when certain conditions are met, and typically used to execute the terms of an agreement). Clicking on this link brings up another page pertaining to the particular smart contract specifically, giving information on users who have purchased the currency and the associated transactions.
Similarly, the ledger website includes pages giving details and connections associated with the domain registrant, etc., which can serve as a basis for building further links.
The second case involved the cryptocurrency ‘Brand2 Coin’ or ‘$Brand2’, which was available to be viewed and purchased through reputable decentralised exchanges (DEXs) such as UniSwap, and was also involved in the sale of NFTs via the OpenSea marketplace. This case also utilised a blockchain domain name (Brand2deployer.eth), but was additionally promoted across Web2 content. In this instance, an associated Twitter account (‘@Brand2-2Coin’) was set up and used to promote the infringing currency, with the smart contract hash (the string beginning ‘0xf484…’) also explicitly given in some postings (Figure 3).
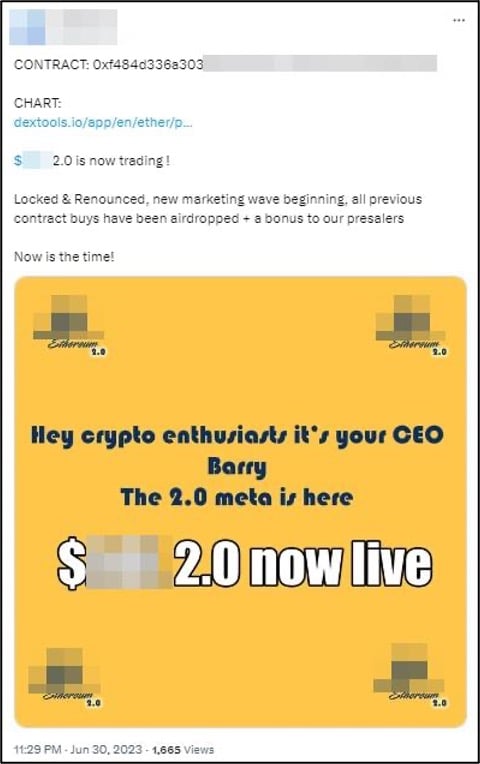
Figure 3: A Twitter (X) post advertising the ‘Brand2 Coin’ infringing cryptocurrency
The Twitter profile also gave the address of an associated Web2 website (Brand2coin.xyz) and a Telegram link (t.me/Brand2coinportal).
Using a similar approach to that shown above, it is possible to search for the smart contract string on the etherscan.iopublic ledger to reveal associated details, such as information relating to the contract creator (‘Brand2deployer.eth’).
This brief overview highlights that, although it may be unusual to establish links from Web3 content to ‘real world’ contact details, application of OSINT-style techniques can still be used to draw connections and reveal additional related findings, and can help to provide information surrounding infringing use of cryptocurrencies.
[1] https://www.iamstobbs.com/opinion/the-crossover-two-recent-developments-in-web2/web3-interaction
[2] ‘Web2/Web3 crossover – Part 2: Brand-related crypto-infringements’
Send us your thoughts:
Would you like to read more articles like this?
Building 1000
Cambridge Research Park
CB25 9PD
Fax. 01223 425258
info@iamstobbs.com
Privacy policy
German office legal notice
Cookie Declaration
Complaints Policy
Copyright © 2022 Stobbs IP
Registered Office: Building 1000, Cambridge Research Park, Cambridge, CB25 9PD.
VAT Number 155 4670 01.
Stobbs (IP) Limited and its directors and employees who are registered UK trade mark attorneys are regulated by IPReg www.ipreg.org.uk



